Colonial Pipeline, Ransomware & the DarkSide
In 2019 ransomware attacks potentially grabbed at least $7.5 billion from victims in the US alone, according to Emsisoft. The average ransom can be anywhere from $200,000 to $2 million.
On May 7th, the largest pipeline system for refined oil products known as The Colonial took many of its systems offline as the result of being the latest victim of a ransomware attack brought on by the Russian hacker group known as DarkSide. The hackers stole almost 100GB of data from the pipeline operator before locking its computer network down, leading Colonial to take its operational network offline out of what it said was an abundance of caution.
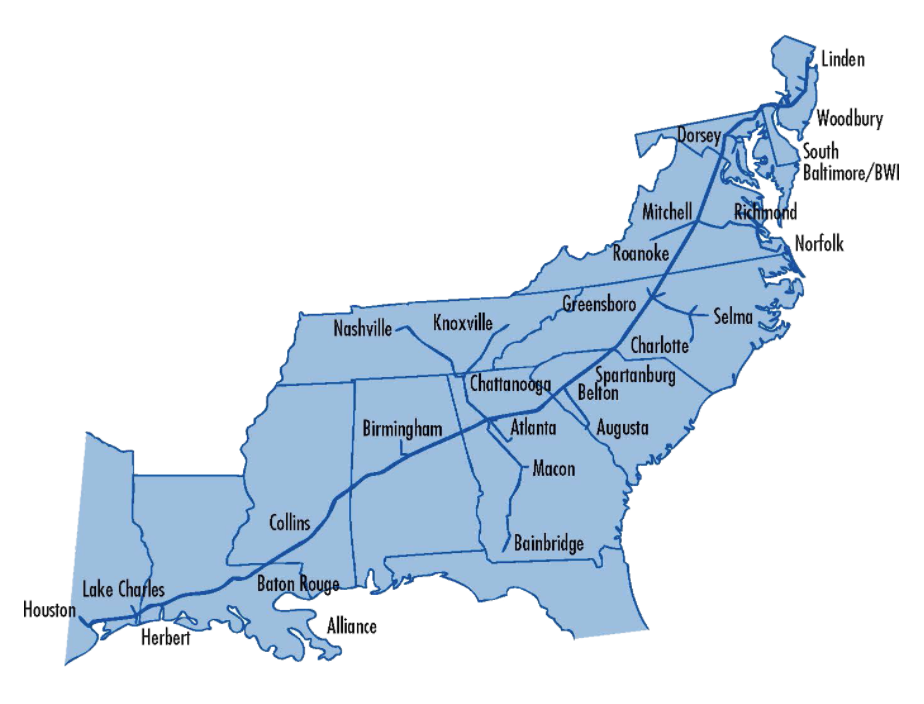
The pipeline transports almost 45% of all fuel consumed by the east coast and had to be shut down leading to gas shortages starting to intensify throughout the Southeast.
Cutting across the Southeast with distribution terminals along the way, for states like North and South Carolina, Alabama, Georgia etc., the pipeline is their primary source of fuel. Installations including Atlanta’s Hartsfield-Jackson Airport and various military bases throughout the east coast were impacted by the shutdown.
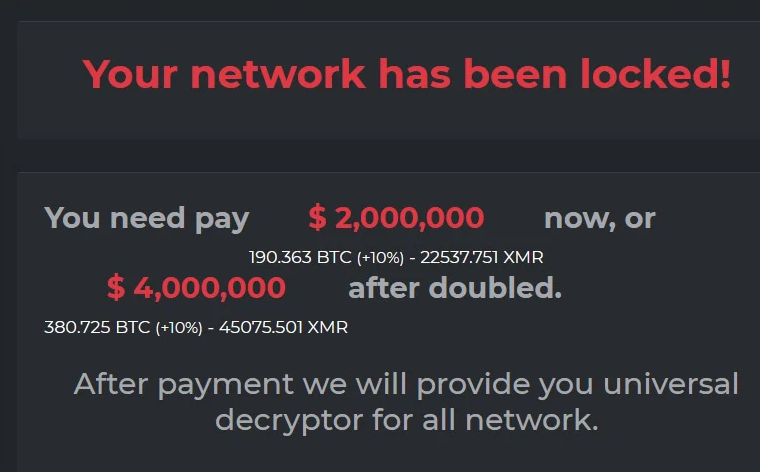
After a six-day outage, Colonial ultimately paid the hackers $4.4 million in Bitcoin for a key to unlock its files. “I will admit that I wasn’t comfortable seeing money go out the door to people like this,” CEO Joseph Blount told The Wall Street Journal.
Ransomware is a form of malware in which hackers gain access into computer systems, encrypt victims’ files, and demand money to restore the data. The Colonial Pipeline hack was not the first significant breach the US has seen but is the largest cyberattack on an energy infrastructure. Last year was an especially vulnerable time for computer systems: schools, hospitals, governments, and private companies had their data encrypted and held for ransom for millions of dollars. Hospitals, in particular, were particularly targeted and ultimately had to pay in order to get lifesaving information, such as drug dosage and medical history.
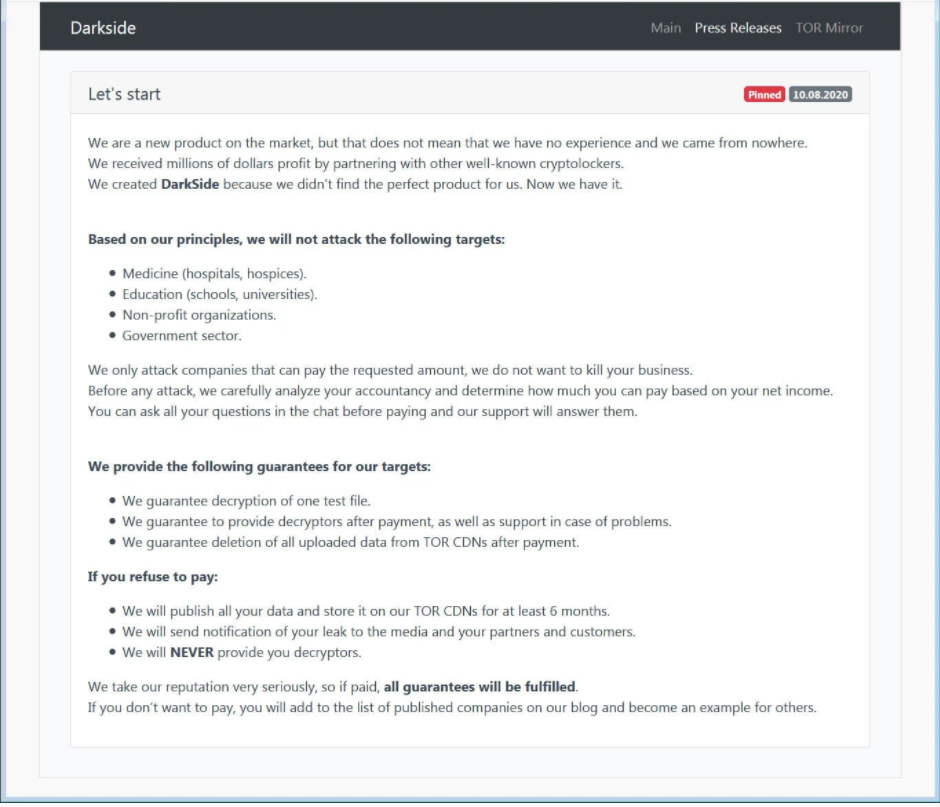
Launched August 2020, DarkSide maintains a data leak site on the dark web listing victims, size of the hack/haul, documents, and information it collected during a breach. In a “press release” on their website posted when they initially launched, DarkSide pledged they would not target hospitals, hospices, schools, universities, non-profit organizations, or the government sector.
Digital Shadows, a cyber security service based in San Francisco, says DarkSide is unique due to its careful selection of targets, custom ransomware, and “quasi-corporate communication throughout attacks.”
Digital Shadows, a cyber security service based in San Francisco, says DarkSide is unique due to its careful selection of targets, custom ransomware, and “quasi-corporate communication throughout attacks.”
There is a professional air to DarkSide as it has employees, costs, profits, and even customer support. Their product is the malware/hacking tools, a “ransomware-as-a-service” model, used during the ransomware and aim is to attack targets that are actually able to pay claiming “before any attack, we carefully analyze your accountancy and determine how much you can pay based on your net income.”
DarkSide hackers have also been known to donate money to charities, posting receipt for $10,000 worth in Bitcoin to Children International and The Water Project through the US based service “The Giving Block” which accepts cryptocurrency donations.
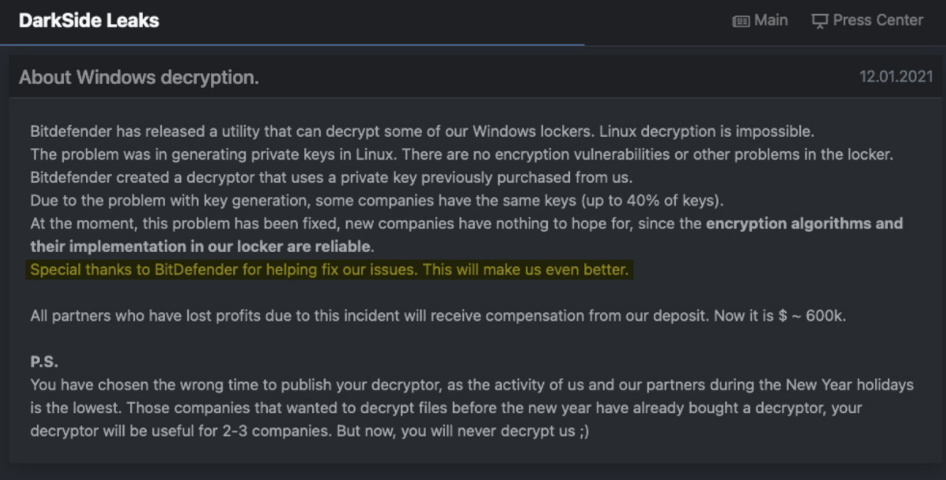
President Joe Biden signed an executive order to strengthen cybersecurity defenses and create an outline for a federal response to cyberattacks. DarkSide said it was shutting down after servers and bitcoin stash had been seized and amid “pressure from the U.S.” Historically, ransomware crews have often disbanded to avoid scrutiny and then re-formed under new names, or their members have launched or joined other groups.
All information and summaries are intended as informational only regarding legal trends and news. Nothing should be taken as legal advice or legal opinion and readers should seek out advice from legal counsel prior to acting on information provided by this blog.